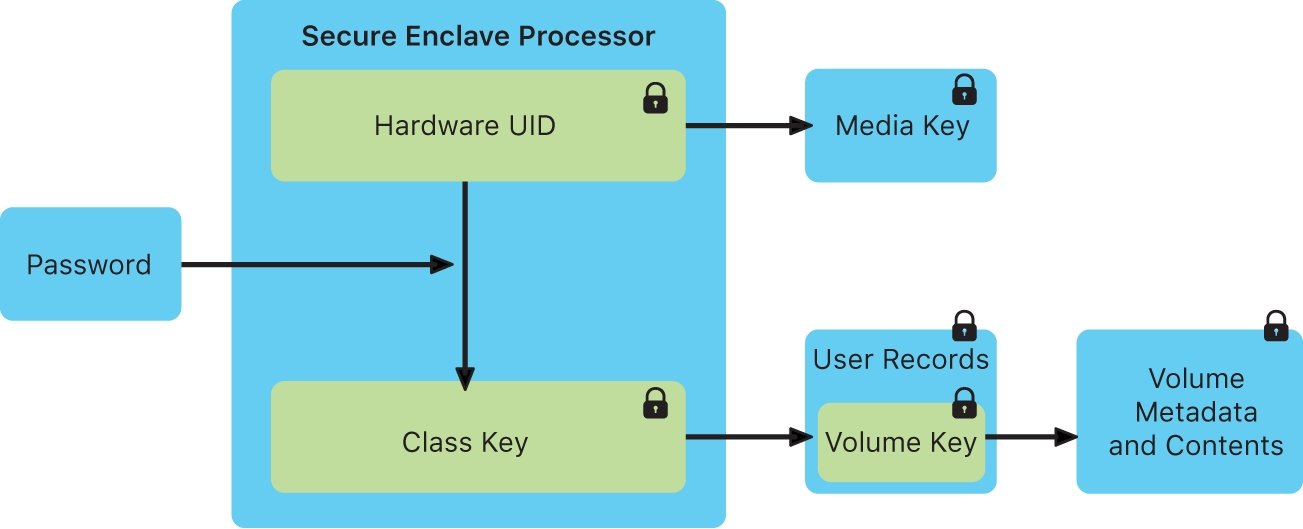
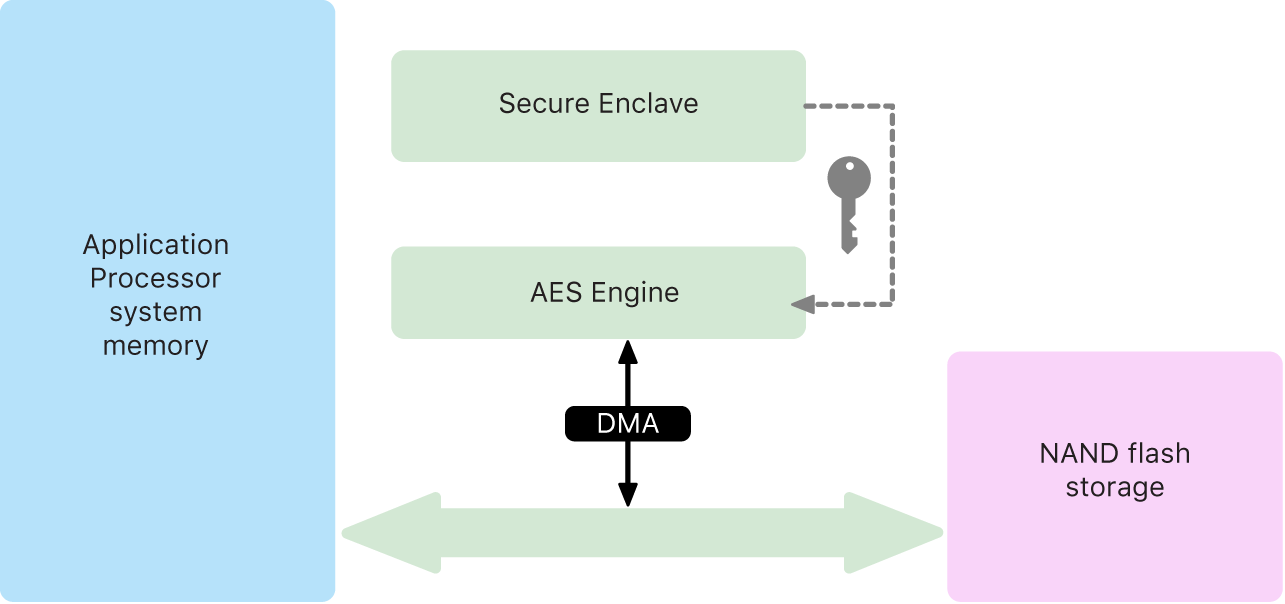
Apple Granted a Patent for a Security Enclave Processor Essential for a Future iWallet Application - Patently Apple
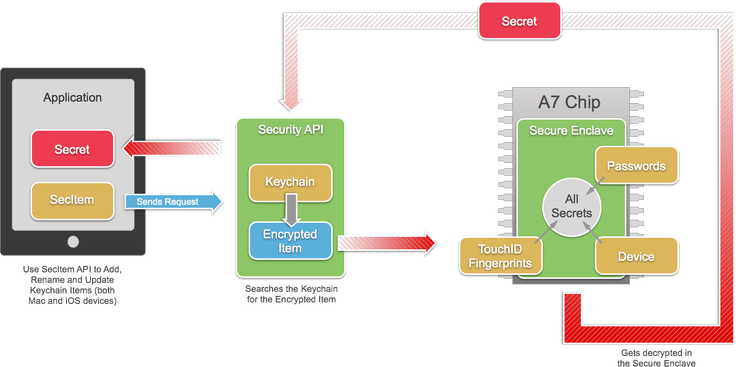
New Patent Reveals Apple's "Secure Enclave" Processor for Touch ID and Possible Fingerprint Accessory - Patently Apple

i.MX Applications Processors with EdgeLock Secure Enclave for Enhanced Safety and Efficiency in Industrial and IoT Applications








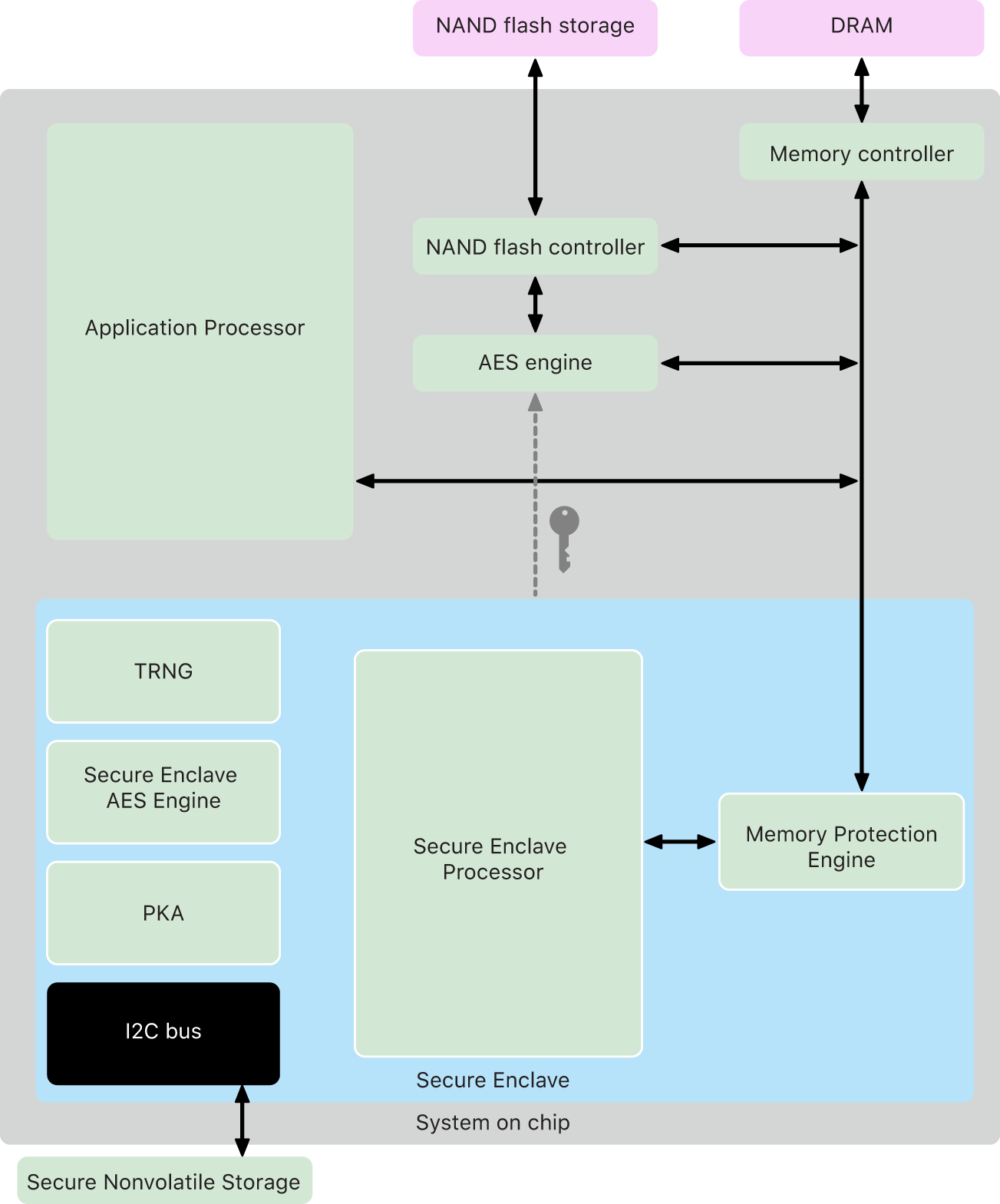

![PDF] Demystifying the Secure Enclave Processor | Semantic Scholar PDF] Demystifying the Secure Enclave Processor | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/c49e4392041d15e26319e048aeefa2e09e181416/15-Figure1-1.png)